Starting with updates for Microsoft Office 2013 and 2010, released in November and December 2014, we're slowly adding a number of improvements to the Document Inspector (also known as the Problem Finder) in Excel, PowerPoint, and Word. The Document Inspector helps you prepare Excel documents, presentations, and workbooks for publishing and sharing by checking for hidden or sensitive information. The Document Inspector removes such objects from the document, and if automatic deletion impossible, warns the user about them. If you want to learn more about the Document Inspector, go to Office.com for how the tool works in Excel , PowerPoint , and Word .
Updates for Microsoft Office 2013 and Microsoft Office 2010 include several review engines, or inspectors, for Excel, PowerPoint, and Word. Below we have listed the objects that the new inspectors check for each of the Microsoft Office applications. Excel has more new inspectors than PowerPoint and Word, simply because some of the objects you inspect are unique to that application.
PowerPoint and Word:
- Embedded Documents
- Embedded Documents
- Macros, Forms, and ActiveX Controls
- Links to other files
- PivotTables, PivotCharts, Cube Formulas, Slicers, and Timelines*
*Timelines are only validated in Excel 2013 as Excel 2010 does not support them. - Functions that use real-time data
- Excel Polls*
* Excel polls are only validated in Microsoft Excel 2013 because Excel 2010 does not support them. - Certain Scenarios
- Active filters
- Custom sheet properties
- Hidden names
Note. Some new inspectors may not be added to Excel 2010 with the November and December updates for Office 2010. They will be added as part of another update in early 2015.
Description of the objects that the new inspectors detect
Conclusion
The Document Inspector helps you delete personal and confidential information from Excel documents, PowerPoint, and Word before publishing. This tool can be very useful as it identifies a range of objects that contain important information and are easily overlooked. However, when you share files, be aware that they may contain data that the Document Inspector cannot find. For example, in Excel you can put something away from the main information, in a row or column that you won’t notice when you skim the sheet before publishing, and in Word or PowerPoint you can insert an image on top of the information and forget that there is something under it there is.
It is also important to understand that a document inspector cannot replace the usual document review by technicians, lawyers, experts, and editors. You should also not neglect the conversion of documents into a format in which there is no hidden information- for example, in formats imitating paper documents (OpenXPS, PDF and others) or in the format of a web page in one file (MHT).
The easiest way to grab the tail of a negligent employee or student who outsourced his report or coursework is to look at the author or co-authors of the document. This information is stored along with other file metadata and can be viewed by anyone later. The case acquires a particularly delicate situation if the real executor turns out to be a person familiar to the inspector: an employee of the same company or a student from the same stream. Of course, a multi-storey lie will find a way out of the situation, but no matter how it then comes out into the light. Pay attention to the associated users of the document in the lower right corner
A banal example, of course, but it is on it that they usually pierce.
What information can be leaked
Microsoft's official help provides information on what could pose a potential threat to your reputation. Here is her excerpt:
- Traces of the presence of other users, as well as indications of their edits and added comments, if you worked on the document as a co-author.
- Discolored information contained in the header, footer, and watermark.
- Word hidden text, PowerPoint invisible objects, Excel hidden rows, columns and sheets.
- Content that is outside the PowerPoint slide area.
- Additional document properties and other metadata, such as printer path information or email headers.
Document Inspector
"Document Inspector" - handy tool to check files for unwanted information. It is convenient for both the sender and the recipient of the document. All you need to do is go to the "Details" and run the check. A couple of clicks and five seconds will turn out the whole ins and outs.

It remains for the performer to click on delete, and for the inspector to examine the document based on the available evidence.
Prohibition of saving personal data
Deletion of personal data
from file metadata
Files created in most popular programs have properties automatically populated from computer data and the program itself. Due to the business need for files leaving the organization, this data should be deleted. For example, in MS Office documents, you need to remove the name of the company, the name of the author of the document, and the user who last saved the document. How to do it?
The solution to the problem of removing metadata from documents can be divided into several stages:
- Removing data from already created documents.
- Avoid saving such data in newly created documents.
- Control of sending such data via e-mail.
For already created files, the task is solved by the built-in tools of modern operating systems. Starting with Windows 7, just call the file properties and at the bottom of the "Details" tab select "Delete properties and personal information". By selecting several files of the same type at once, you can erase data from several documents at once.
To bulk delete information from files, you can use special applications. For example, BatchPurifier allows you to automatically remove the metadata of 60 values from 24 file types, including office applications and graphic files(PNG, JPEG).
For new documents in the Microsoft Office application, users must use the "Document Inspector" tool from the "Details" - "Search for Issues" menu, which scans the document that has not yet been saved for personal data and deletes them.
In earlier Microsoft versions Office (XP or 2003), you need to install the Office 2003/XP Add-in: Remove Hidden Data, rhd_tool , after which an additional Remove Hiden Data item will appear in the File menu.
In order to prevent the registration data of Microsoft Office applications for newly created documents from identifying the user, you can make the following changes in the registry:
Windows Registry Editor Version 5.00
"Company"="_"
"CompanyName"="_"
"Username"="_"
"UserInitials"="_"
MS Office applications must not be running for the changes to take effect.
The next step is to control the sending of hidden data or personal information via e-mail.
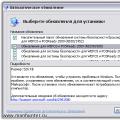
Unfortunately built into Microsoft Outlook there is no solution. For automatic control and cleaning of documents, you can use the ConfidentSend application, which can manually or automatic mode clean up attachment file metadata. ConfidentSend also checks the message for a match with predefined user text templates and, if found, issues a warning (see Fig. 2).

The Details tool allows you to view and modify important document properties, thereby preparing it for collaboration, archiving, or sending e-mail. The tool provides access to several commands, which will be discussed in more detail later in the text of the book, but here we will only briefly describe their purpose.
Properties
The right side of the Details window. Each document, in addition to the actual content, carries a lot of information about who created it, what is its topic, to which category it can be attributed. In addition, the document includes keywords characterizing the content of the document, notes, etc. All this information helps automated document management systems or users to place, sort and search for the right documents. For this reason, I advise you not to be lazy and fill in the appropriate fields. The smarter you fill them out, the easier it will be to work with the document.
Prepare for sharing
Document Inspector- this command opens the document inspector window. Some personal information and information about your computer is inserted into the document automatically, without you noticing. For example, the username under which you created the document is contained in the document whether or not you filled in the property fields. If you have printed the document, or even previewed it, the full path to the local or network printer. If you inserted illustrations into the document, then the path to them is also stored in the document. If you are mailing a document to a large number of different people, you may not like that information being made available without your knowledge. Document Inspector searches for hidden data in a document, presents it to you and allows you to delete it
them from an Excel workbook.
Examination accessibility - allows you to evaluate how convenient it will be to use these documents for users with disabilities.
Compatibility check- the command checks if it is possible this document without making changes to it open in more early versions Excel.
Protect book
This tool allows you to impose restrictions on the ability to change and edit the content and structure of the book.
Encrypt with a password- the document is encrypted so that you can see its contents only after entering the password. When encrypting a book with a password, be very careful about the current letter case and keyboard layout, otherwise you risk losing access to your own book.
Restrict permissions for users- this command is usually available only to the author of the document and users corporate network or the Internet. It uses a user rights management server. It can be a free Microsoft server or a corporate server. Every time the user tries to open the document, a request is sent to the server and it returns the properties this user, in particular, information about what he can see in the opened document, and what should be hidden from him. When you try to run this command, you will be prompted to register with the Microsoft server. If you are interested in seeing how the restrictions work, go through this procedure, register several users with different rights, and test this command.
Add digital signature - this command adds an invisible code to the document that replaces the usual signature. Carefully read what the signature creation wizard will write to you. If you create a personal signature, then with its help only you personally and only on this computer can make sure that your document has not been tampered with. If you want to create a signature that will be "recognized" by external organizations, you will have to use the services of special network services.
Mark as final- after executing this command, it will be impossible to make changes to the document.
Protect current sheet- using this tool, you can specify which elements of the sheet can be changed by other users, and which are protected and cannot be changed.
Protect book structure- prohibits changing the structure of the book (adding or deleting sheets).
Versions
Allows you to view and restore draft versions of unsaved files or delete draft versions that are no longer needed.