Ensuring the confidentiality and security of received and transmitted data is an important condition for working on the Internet. This is especially true in relation to state and municipal entities, legal entities who regularly exchange various types reporting, sending and receiving various payments. To ensure protected activities of the listed entities Russian company"Security Code" has been developed by a number of hardware and software products. Allowing you to ensure the protection and safety of transmitted data, avoiding leakage or hacking. One of these products is Continent-AP software 3.7, and below we will look at what Continent AP 3.7 is and whether it is possible to download Continent AP 3.7 from the official website.
What is Continent AP 3.7?
The Continent-AP software is designed to ensure secure data transmission through public networks by building a secure VPN network. The protection of transmitted data is ensured by cryptographic encryption, which prevents data leakage in favor of third parties.
The reliability of Continent-AP is confirmed by various certificates of the FSB of Russia. It recommends the functionality of Continent AP 3.7 for working with the treasury service and various state and municipal bodies.
The operation of the Continent-AP software is based on the client-server principle. Installed on the client computer software package“Continent-AP”, which connects to the desired server. The latter checks the client's authority to access network resources, and if the decision is positive, grants the specified access.
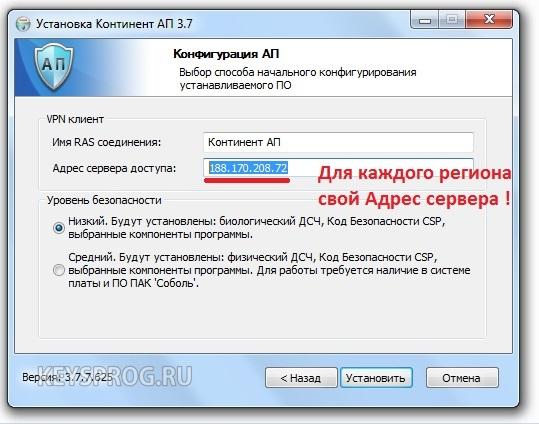
Before installing the latest version of Continent-AP (currently version 3.7.7 and higher), the tool must be installed on the client PC cryptographic protection information (CIPF) " CryptoPro CSP» version 4.0 and higher.

APKSH "Continent" - hardware encryption module
How to get Continent AP 3.7
The official procedure for obtaining Continent-AP software 3.7 boils down to approximately the following:
- An official application is submitted to the appropriate department (for example, to the federal treasury department of your region) for the provision of the cryptographic protection tool for the CIPF “CryptoPro”;
- A letter is often attached to this application, in which the head of the federal (municipal) structure indicates the name and position of the person who is entrusted with receiving the disk with the appropriate software;
- Upon receipt, the responsible person must have with him a blank CD (DVD) disc on which to record software;
- The responsible person installs the specified software on the appropriate PC in his structure. To do this, you need to insert the recorded disc into the CD (DVD) drive of your PC, run the setup.exe file, and go through the installation procedure;
- Then you will need to run Setup\ts_setup.exe and install the Continent AP 3.7 software on your PC.
How to download Continent AP 3.7 from the official website
As you can see, the procedure for obtaining this software product does not involve directly downloading Continent AP 3.7. from the developer's official website at securitycode.ru. However, there are network resources, offering to download Continent AP 3.7 from the network. For example, you can download a version of the product from the resource kontinent-ap.ru or use a direct link to the archive
Continent AP 3.7 is software that makes it possible to organize the protection of separately organized information networks from hacking from any other networks, including from global network Internet. It ensures complete confidentiality of information over VPN channels, creates a secure VPN route for access to other public networks, and allows for protection during the interaction of various types of networks.
Possibilities
The Continent complex allows you to combine VPN networks and other firewalls. It is often used by various government agencies, including the Russian Treasury. When using the program, user authentication occurs based on public keys. All access policies and other parameters are adjusted by the network administrator using specialized NCC software from the Continent package. All data in this program is encrypted using a special scheme that was developed in accordance with GOST. Therefore, access to any transmitted data is not available to attackers.

Other options:
- proxy authentication is supported;
- all traffic can be tunneled to HTTP;
- you can configure the program so that the client (program) can automatically connect to a secure network without operator assistance;
- it is possible to join a network (access server) using a DNS name;
- there is an API for working with external applications;
- workstations can participate in work remotely (in a domain);
- the application also works on others operating systems ah, for example, on Linux;
- the ability to distribute IP packets by protocol type: ICMP, TCP, UDP;
- filtering using the following protocols: SMTP, POP3, HTTP.
Peculiarities
Data protection is implemented using crypto-resistant algorithms. The Continent program supports all kinds of key carriers. They can be flash drives, electronic keys iKey, eToken, ruToken, iButton. For computers you can install TM Card or Sobol. It is possible to access from mobile devices(but data transfer may be limited in speed due to mobile data transfer standards). In encrypted mode, users can communicate with the server at a speed of 16 Mbps.


The software supports dynamic IP assignment. A unified interface for managing and setting rights and access filters to a single database. Access can be provided via various communication channels (dedicated, dial-up), which use Internet access methods via xDSL, Dial-UP, as well as GPRS, WiMAX, 3G, Wi-Fi and satellite signal. Built-in firewall.

Purpose
Initially, the developers wanted to create a highly specialized product that could only combine several enterprise networks into one secure one. Afterwards she grew additional functions and capabilities and has become a full-fledged complex for creating the most secure network with large quantity settings and your own access policy.
- powerful algorithm for encrypting data over the network;
- ample opportunities for working with VPN and its configuration;
- support for all data transfer protocols.
- limited set of tools and functions for Unix-like systems;
- there is no way to set the time in the graphical interface;
- does not support the CLI interface.
Download
Continent AP 3.7 is a software package for ensuring security in corporate networks with a wide range of options and settings.
| Language | Russian |
| OS | Windows 7, 8.1, 10 |
Purpose
- Securing connections to remote workstations
In cases where only 1-2 employees work in a remote office and for some reason installing the Continent APKSH is impractical, a secure connection of the workstation to resources is possible automated system enterprises using the Continent-AP VPN software client. - Securing connections to mobile clients
Providing the ability to securely connect to information resources enterprises for mobile employees and company management. The Continent-AP VPN software client can be installed on the laptops of mobile employees.
Possibilities
- Cryptographic data protection
Cryptographic protection of transmitted data is implemented on the basis of Russian cryptographic algorithms in accordance with GOST 28147-89 in gamma mode with feedback. - Authentication/identification of remote users
Identification and authentication of a remote user when establishing a connection between the subscriber station and the Continent access server is carried out on the basis of public key certificates. The scheme is implemented using X.509 standard certificates. There are 2 options for working with certificates: the trusted certification authority is the access server management program - the first option and the trusted authority is an external certification authority - the second option, in the second option integration with CA CryptoPro is possible. - Supports a variety of key media
As a carrier key information A VPN client for Windows or Linux can be floppy disks, flash drives, electronic keys eToken, ruToken, iKey, and it is also possible to use iButton identifiers if the PC allows you to install the Sobol PAK or TM Card.CIPF "Continent-AP" for Adnroid supports the ability to store key information on secure JaCarta MicroSD cards from Aladdin R.D.
- Remote user access to protected network resources via an encrypted channel.
- Remote access mobile users.
- Communication with the Continent access server at speeds up to 16 Mb/s* in encryption mode.
*For a VPN client for mobile devices, the connection speed is limited by the quality of the communication channel (3G, GPRS, Wi-Fi, etc.).
- Support for dynamically assigned IP addresses.
- Centralized management of filtering rules and user access rights to information resources of a secure network.
- Transparent traffic exchange with protected network segments for any application (including VoIP and video conferencing).
- Access via both dedicated and dial-up communication channels using in various ways connecting to the Internet using technologies: Dial-UP, xDSL, leased line, Wi-Fi, GPRS, 3G, WiMAX, satellite communication channels.
- Integrated firewall
The Continent-AP software for Windows OS includes a firewall (FWE) designed to filter IP packets from the network traffic of the computer on which Continent-AP is installed. ITU provides filtering of incoming and outgoing IP packets based on the following criteria:- IP addresses of the sender and recipient;
- application protocol type (POP3, HTTP, SMTP, etc.);
- the network interface through which the packet was received or will be sent;
- header fields and contents of IP packets.
- by transport protocol type (TCP/UDP/ICMP/…);
- via TCP/UDP ports;
- by types and codes of the ICMP protocol.
- Ability to connect to the access server viaDNS-name.
- It is now possible to tunnel traffic toHTTP-tunnel.
- Authorization support forHTTP- PROXY.
- ImplementedAPIinterface for interaction with external applications.
- Possibility of automatic installationVPN- connections to workstations without operator participation.
- Possibility of establishing a connection between CIPF “Continent-AP” for Windows and Linux with the access server before registering the OS user.
Allows workstations belonging to a domain to work remotely.
System requirements
CIPF "Continent-AP" for Windows or Linux operating systems can be installed on computers equipped with processors of the Intel X86 family or compatible with them.
| Element | Minimum | Recommended |
|---|---|---|
| CPU | Celeron 300 MHz | Pentium IV 1.8 GHz |
| RAM | 128 MB | 512 MB |
| HDD (free space) | 512 MB | 512 MB |
| operating room system | Windows:
Linux:
|
|
CIPF "Continent-AP" for Android is installed on tablet computers and smartphones with Internet access.
| operating system | Android 4.x and higher |
|---|---|
| Memory | Or External card memory, or any inner memory, accessible to applications (for example, the user section) |
| Means of Internet access | Any of:
|
Documentation
The documents presented here are included with the product. They are subject to all terms of the license agreement. Without the express written permission of Code Security, these documents or parts thereof in printed or in electronic format cannot be copied or transferred to third parties for commercial purposes.
The information contained in these documents may be changed by the developer without special notice, which does not constitute a violation of the obligations towards the user on the part of the developer company.
User documentation
Version 3.7 RU.88338853.501430.007
ReleaseNotesAP.pdf
| Administrator's Guide The manual contains the information necessary for the administrator to install and configure the Complex components on the Windows platform. Continent-AP_Windows_Admin_Guide.pdf |
|
| User guide The manual contains the information necessary for the user to operate the Complex software on the Windows platform. Continent-AP_Windows_User_Guide.pdf |
CIPF "Continent-AP" for Android, version 3.7
ReleaseNotesAP.pdf - This document contains a description of the main features and limitations (Release Notes).
Certificates
| DEPARTMENT | NUMBER | PRODUCT | DESCRIPTION | VALID |
|---|---|---|---|---|
| FSTEC of Russia | 3007 RU.88338853.501430.007 | CIPF "Continent-AP" version 3.7 | Confirms compliance with the requirements of the guidelines for level 3 control for the absence of non-intrusive substances and class 3 security for firewalls. | Until 01.11.2016 |
Application options
APKSH "Continent" is a powerful and flexible tool for creating virtual private networks, allowing you to build a VPN of any architecture. Below are typical schemes for constructing a VPN based on the complex:
Wireless Security
Secure client connection wireless network into a dedicated segment with different access rights.
Connecting remote users
Connection remote clients to a network protected by APKSH "Continent" using a subscriber point. Working with dynamic IP addresses significantly increases user mobility.
Centralized AP connection
For small businesses or small enterprises, a centralized AP connection scheme is ideal.
Connecting the AP according to the “tree” diagram
For organizations with an extensive network of branches and representative offices, it is possible to organize a VPN according to the following scheme: "tree". Such a scheme will streamline information flows within the organization.
Decentralized AP connection
If an organization has a complex distributed information system collecting and processing data or to solve complex problems, it is possible to organize access to VPN resources in a decentralized manner.
Continent-AP" for Android OS
Key Features
| Cryptographic protection Traffic encryption in accordance with GOST 28147-89 with a modern key scheme ensures guaranteed cryptographic strength of a secure connection | Working without superuser rights Installation and operation of the VPN client is carried out by the user regular means Android and does not require root rights, which ensures the safety of the mobile device |
||
| Strengthened Authentication Identification and authentication of the remote user when establishing a connection is based on public key certificates of the X.509 standard | Centralized management All access policies for mobile users are configured by the administrator of the organization’s VPN network using the Continent SD management program |
Screenshots |
Documentation
Video instructions
To view video instructions for installing and configuring the Continent-AP CIPF VPN client on a mobile device running Android OS, select the material you are interested in:
1. Installation of CIPF “Continent-AP” for Android on a mobile device.
2. Creating a request for a certificate in the CIPF application “Continent-AP” for Android
3. Creating a connection profile in the Continent-AP CIPF for Android.
4. Connecting the user of the CIPF "Continent-AP" for Android to the Access Server "Continent" 3.7.
This is a protective complex that protects your local network from hacker attacks from other connected networks, including the Internet as a whole. In addition, a fully secure VPN connection is provided. The program also contains a number of other functions, which we will discuss in this article. At the very end of the page you can download the latest Russian version of Continent AP 3.7 for free via a direct link.
Possibilities
This protection technology is used by many banking institutions to prevent hacking. own systems. The protection used here is based on public key technology. All users who access the network are controlled directly by administrators from a special panel called NCC. It uses its own protection algorithm, developed specifically for Continent AP. That is why it is impossible to bypass it.
The application also contains a number of additional features, among which:
- work through a proxy server;
- HTTP and HTTPs tunneling mode is supported;
- you can configure the package so that a specific user connects in automatic mode without the involvement of an operator;
- you can connect to other networks not only via HTTP, but also via DNS;
- there is an API for connecting third-party applications;
- you can manage any users not only from the same network, but also remotely;
- Operating systems supported Windows systems XP, 7, 8 m 10, as well as Unix-like;
- Filtering of access addresses by protocols: ICMP, TCP, UDP.
During operation, the application in question uses a set of its own security algorithms, which increases its reliability. The continent can store access keys on various external devices. These can be memory cards, USB flash drives, iKey, eToken, ruToken or iButton keys.

On Personal Computer or a laptop can be installed with TM Card or the Sobol system. You can also access it from mobile devices. However, in this case, due to the characteristics of such operating systems, maximum speed access is not guaranteed. In encryption mode it reaches values of 17 Mb/s.
The program sets the IP address independently, randomly selecting it from the existing database. Access and moderation is carried out through a single panel. It can connect via any channels, including dial-up and leased lines. The connection method can be anything, it can be 3G, LTE, or even the outdated EDGE GPRS.

At first, this software was a narrowly focused solution that ensured the security of individual corporate networks. Over time, the program acquired more and more new functions, which ultimately led to its popularity and emergence as the most reliable solution for protecting all types of networks.
Advantages and disadvantages
Let's also look at a list of the program's characteristic strengths and weaknesses.
Advantages:
- highest degree of safety;
- complete Russification;
- VPN support;
Flaws:
- poor functionality on Linux;
- difficult to set the time.
Video
In order to understand how to install the program and work with it, we recommend watching this video.
Also in the archive you will find detailed instructions for working with the application.
Keys
You don't have to activate the software. This is RePack and the “treatment” has already been done.
Download
Now you can download the latest Russian version of Continent AP 3.7, since you already know enough about the program.