Released updated version Security Capsule SIEM v.3.0. The mechanisms of the system have been radically redesigned. A new web interface has been completely developed. We work for you, setting the trend in the SIEM systems market. Rich experience in development and implementation since 2009 makes us leaders in this segment.
In accordance with clause 15 of the Regulations on the certification system for information security means of the FSTEC of Russia, ITB LLC confirms the provision technical support certified information security tool “Security Capsule” until November 09, 2022.
LLC "Innovative Technologies in Business", being a developer and manufacturer, has successfully completed certification of serial production operating system EMIAS OS 1.0 automated system of the city of Moscow “Unified medical information and analytical system of the city of Moscow.”
ACTIVITY
LLC "ITB" will take part in the event "SPbSEU Career Week - 2019", held by the St. Petersburg State Economic University from November 11 to 15, 2019.
On September 18-20, 2019, specialists from ITB LLC took part in a partner event from Security Code: A sea adventure with Security Code. “Security Code” organized an exciting Sea adventure for its partners: the traditional event was held in a new format this year. For the first time, the #KB landing force was assembled outside of Russia under the gentle sun of Turkey.
From February 13 to 15, 2018, experts from ITB LLC took part in the TB Forum 2018 - the 23rd International Forum “Security Technologies”. TB FORUM has rightfully earned a reputation as one of the leading congress and exhibition events in the field of security. For more than twenty years of history, it has been and remains the only open security industry event for customers high level- state and largest corporations.
After purchasing a license in our online store, you will receive a letter by e-mail, in which you will find:
- license key product
- link to product distribution
- link to user manual
Step 1
First you need to find out whether you have installed Cryptopro CSP earlier and if installed, what version?
This can be done by carefully examining your Start menu: there should be an item CRYPTO-PRO, which has a program CryptoPro CSP.
If you don’t find it, most likely you don’t have CryptoPRO installed, so feel free to go to.
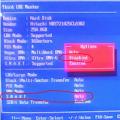
If you find it, run it CryptoPro CSP. There we see the General tab, where the license validity period and version number are indicated.
If the version number matches the version you purchased (for example, if the window says 4.0.****, and you bought CryptoPro CSP 4.0, it means it matches), then you you don't have to reinstall the program, but simply enter the license key. How to do this - look at .
Step 2
You find out that the program is not installed. This means you need to download CryptoPro CSP and install it.
Downloading it is not so easy: the crypto provider is a means cryptographic protection information, which means its distribution is subject to registration with the relevant authorities. Therefore, you will need to follow the link that came to you in the letter or go to the CryptoPro website yourself using the link http://www.cryptopro.ru/downloads and select from the list of products CryptoPro CSP.
You will see something like this:

Click on the link " Pre-registration" and fill out the form from a variety of fields. After filling out the form and registering, you will be required to agree with license agreement, and then still get the opportunity to download the distribution package of the program.
At the time of publication, the distribution selection page looks like this:

If you purchased the version CryptoPro CSP 3.6, then you will need to select a version R4- today it is the most functional.
If you purchased a license for CryptoPro CSP 3.9 be careful: CryptoPro CSP 3.9 - certified version, but does not support Windows 10, CryptoPro CSP 3.9R2 - supports Windows 10, certification planned for Q4 2015
If you bought version 4.0, then select CryptoPro CSP 4.0 accordingly (recommended for working with Windows 10, certification is planned for the third quarter of 2015).
You will need to download this file:

Step 3
You have downloaded installation file CryptoPro CSP, and now you will need to install the program itself. To do this, run the installation file; if we see a security warning, you need to allow the program to make changes on your computer. In the window that opens, click the button Install (recommended)

Installation of the program occurs automatically within a few minutes and does not require user participation.


All, Installation completed.
Step 4
Now you need to enter the license key in a special window. You can get to it this way (the path may vary slightly depending on the version of the operating system):
Start - Programs - CryptoPro - CryptoPro CSP.
Then press the button Entering a license

In the window that opens, fill in the fields in accordance with the received license.

Step 5
We rejoice! We have just installed a crypto provider. Not that hard, right?
But you need to understand that CryptoPro CSP itself cannot do anything. The next step is to install (or simply configure) programs that will interact with CryptoPro CSP and solve your problems, be it electronic signature, encryption or something else.
Usually, to carry out an electronic signature, they use or - they can be purchased from us in the online store. We tried to make the purchase as convenient as possible: electronic licenses are sent immediately after payment (even at night), a large selection of payment methods.
If you found the instructions useful - share it, you will find buttons for this right below the article.
IN following instructions I will tell, how to install CryptoPro Office Signature , CryptoARM, how to work with tokens and so on.
If you don't want to miss our articles, subscribe to us at in social networks! Links to our social media pages can be found at the very bottom of the screen.